Credential Management is a key information security domain. In this blog post, I would like to explain how to securely access Secrets from Azure Key Vault from Power Platform Custom Connector using OAuth 2.0 Client Credential Flow (Service Principal). Complete source code GitHub link is provided at the end of this post!
Create a new App registration in Microsoft Entra ID and record the below information. We will need this information to configure OAuth2 settings.
- Display name:
- Application (client) ID:
- Object ID:
- Directory (tenant) ID:
- Client Secret:
In Azure Portal:
- Create a new Key Vault in Azure. I am creating a key vault using Azure Portal.
- Under Access Control (IAM) –
- Grant your own account RBAC (permission) to key vault data plane (i. e. Key Vault Administrator).
- Grant the Service Principal (created via App Registration) read access to key vault data plane. This is needed by Custom Connector to access key vault.
- Add a new secret and add the value
Login to Power Apps and Create a new custom connector
Overview tab:
Add description that is more than 30 characters
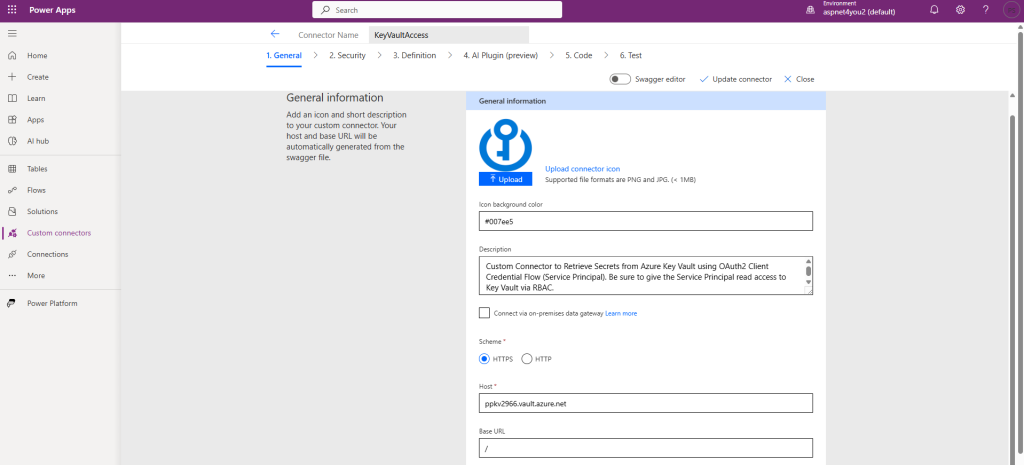
Scheme: HTTPS
Host: your-key-vault-base-url (ppkv2966.vault.azure.net )
Base URL: /
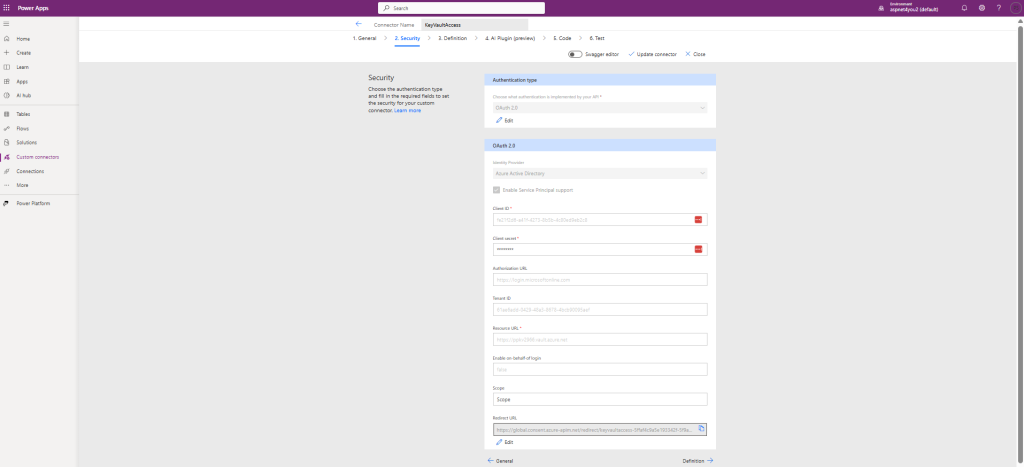
Security Tab:
Select OAuth 2.0 from Authentication type
Identity provider: Azure Active Directory
Check – Enable Service Principal support
Enter Client ID:
Enter Client secret:
Authorization URL: https://login.microsoftonline.com (auto populated when you select Azure Active Directory as Identity provider)
Enter Tenant ID: leave as common
Enter Resource URL: example, https://ppkv2966.vault.azure.net
Enable on-behalf-of login: false
Scope: leave it empty
Redirect URL: will be auto created after you save/create the connector
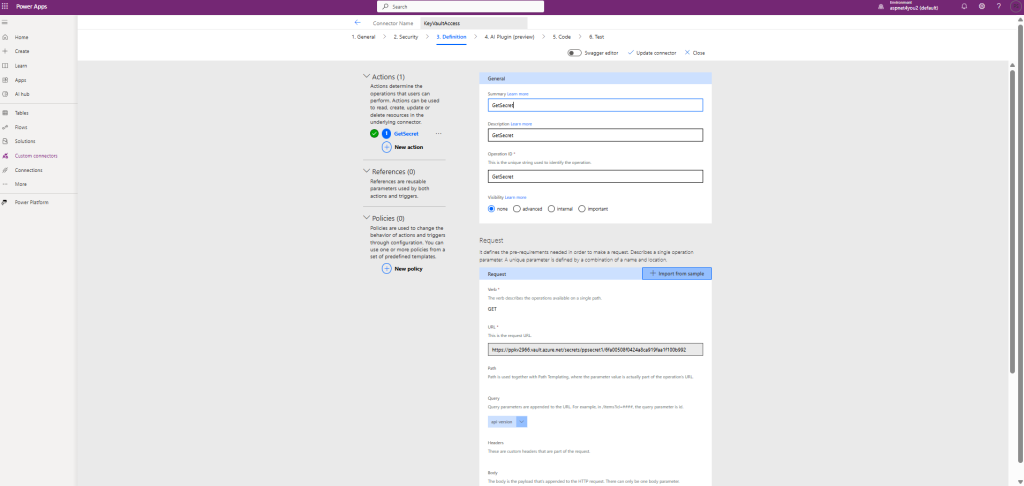
Definition tab:
Summary: GetSecret
Description: GetSecret
Operation ID: GetSecret
Visibility: none
Request: + Import from sample
Add: GET https://ppkv2966.vault.azure.net/secrets/ppsecret1/6fa00508f0424a8ca919faa1f100b992?api-version=7.4 (change to your key vault)
You don’t have to do anything at AI Plugin(preview) and/or Code tabs.
Create/update connector
Before you can Test, you must create a Connection. You can do so at Test Tab itself or you can go to Connections tab and create new connection. I would rather do at Test tab.
Test tab:
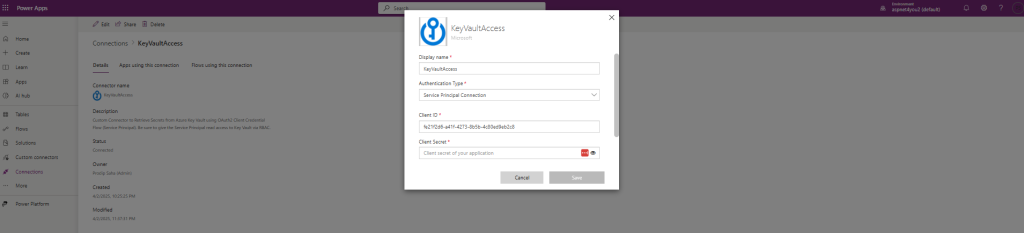
Create/Edit Connection:
Display name: KeyVaultAccess or anything you like
Authentication Type: Service Principal Connection
Client ID: [from Microsoft Entra ID App registration]
Client Secret: [from Microsoft Entra ID App registration]
Tenant: [from Microsoft Entra ID App registration]
** Note: Client ID and Client secret are not saved in the definition**
Once connection is created successfully, you can go back to Custom connector and jump to Test tab directly
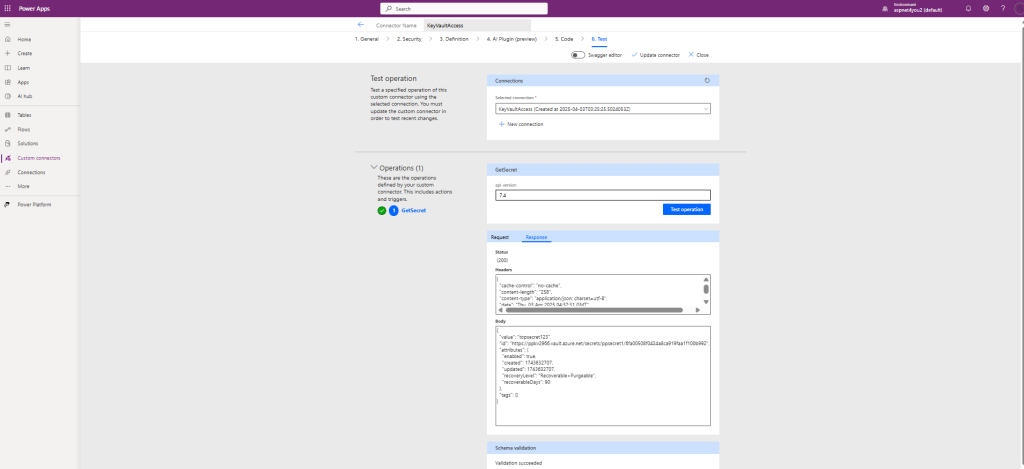
Make sure Selected connection is populated with the connection name that you just created (along with created at date/time). You would see GetSecret under Operations.
Enter api-version: 7.4
Click Test operation button
You should get valid response header and body. Secret value would be in the response body. Wow! You have successfully retrieved secret from Azure Key Vault.
You can find complete source code in GitHub at https://github.com/aspnet4you/PowerPlatformAzureKeyVault
Limitations:
OAuth 2.0 authentication is not available when custom connector is configured with Connect via on-premises data gateway. What does it mean in corporate environment?
In corporate environment, Azure Key Vault public access is disabled as security best practice. That mean service principal at the custom connector connection can’t access the key vault. I plan to share how to overcome this limitation in next blog post!
Comments are disabled at the blogs to avoid spams. If you have any feedbacks or comments, you are welcome to contact me over LinkedIn.
