Managing external workloads securely while enabling seamless authentication is a challenge many organizations face. Microsoft Entra ID Federated Credential provides an elegant solution for integrating external identity providers, such as AWS Cognito, into Entra ID authentication flows. In this blog post, we’ll explore how this integration works and how you can leverage it for secure, scalable identity federation.
You can’t use Azure as external identity provider unless you are using Managed Identity. Feel free to read my previous blog post – Manage Cross Tenant Resources using Entra ID App with Federated Credential and Managed Identity. Let’s cut to the chase! We will cover the design/architecture first and implementation details will follow.
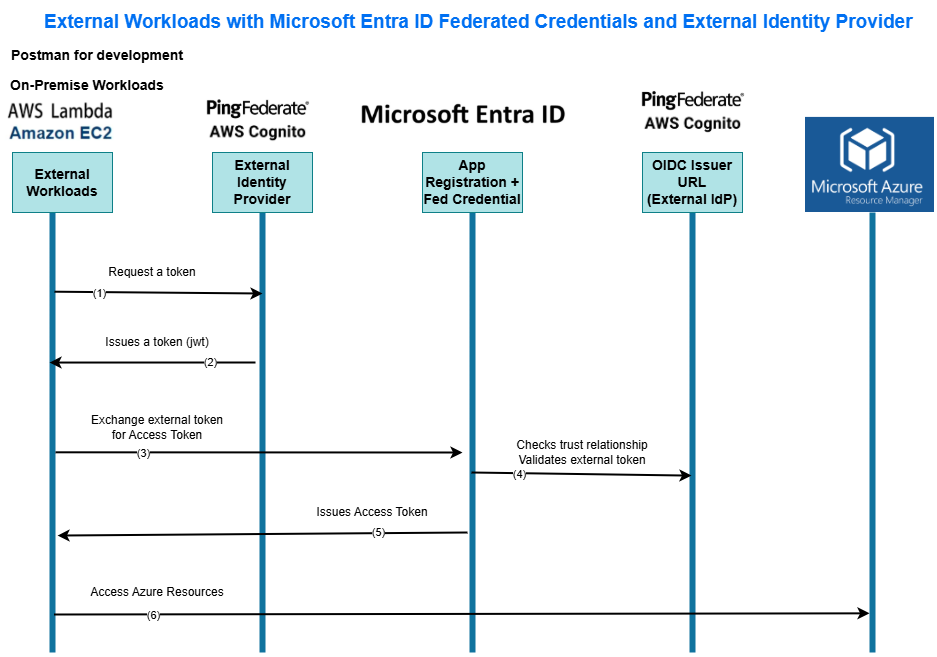
(1) External workloads (i.e. AWS EC2/Lambda) requests a token from an external identity provider (i.e. AWS Cognito, Ping Federate, Okta, etc.). I don’t have a web app in AWS, I used AWS cli to get-open-id-token-for-developer-identity from AWS Cognito.

(2) External Identity Provider, AWS Cognito in this case, issues a jwt token. Used jwt.ms to visualize the jwt token issued by Cognito.

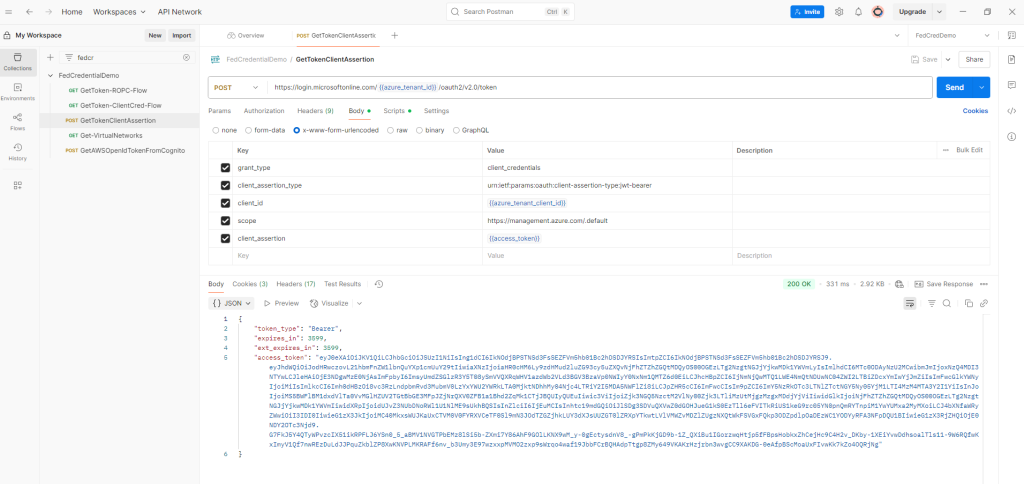
(3) External workload uses this jwt token issued by Cognito and exchange it for an access token from Microsoft Entra ID. I am using Postman just for the concept testing to get access token from Entra ID by exchanging the token received via AWS cli in step 1. We will use Azure Resource Management as scope of the request.
(4) Microsoft Entra ID reaches out to external IdP (Cognito in this case) to validate the jwt issued by AWS Cognito.
(5) Microsoft Entra ID issues access token. Workload would use this token to call Azure Management API.

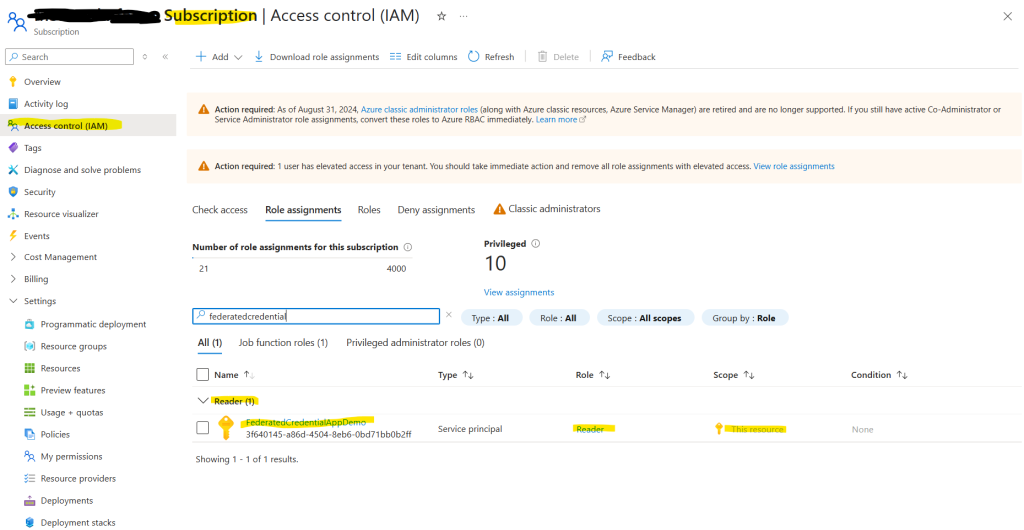
(6) Access Azure Resources using access token received in step 5. Be sure to grant IAM permission on Entra ID Application to Azure Subscription or Resource Group.


Understanding Microsoft Entra ID Federated Credential
Microsoft Entra ID Federated Credential enables external workloads to authenticate using identities from third-party providers without requiring direct user interaction. This approach is ideal for applications running in environments like AWS/GCP/On-Premise, allowing them to verify their identities and securely access Microsoft resources.
The key benefits include:
- Eliminating password-based authentication for workloads.
- Granting seamless access to Microsoft Azure resources.
- Enhancing security by using verified identity tokens from trusted providers.
Why Use AWS Cognito as an External Identity Provider?
AWS Cognito offers a robust identity management platform for applications running in AWS. By federating Cognito users with Microsoft Entra ID, organizations can extend their authentication model while maintaining centralized identity governance. Note- I am using AWS Cognito for this demo, but, at the corporate setup, I would be using enterprise IdP like Ping Federate which can be customized to fulfill subject and audience requirements dynamically.
Key advantages include:
- Scalability: Cognito can handle large numbers of users and identities.
- Multi-factor authentication support: Enhancing security while federating credentials.
- Integration with AWS services: Useful for applications running on AWS that also require access to Azure resources.
Why Use PingFederate as an External Identity Provider?
PingFederate is a leading identity federation platform that supports OAuth 2.0, OpenID Connect, and SAML-based authentication. Integrating PingFederate with Microsoft Entra ID ensures flexible, secure authentication for workloads running externally.
Key advantages include:
- Enterprise-grade security: PingFederate provides strong encryption and access control.
- Identity federation across multiple protocols: Supporting SAML, OAuth, and OpenID Connect.
- Integration with on-prem and cloud environments: Useful for hybrid and multi-cloud scenarios.
How to Set Up Entra ID Federated Credential with AWS Cognito
Step 1: Configure AWS Cognito
- In AWS Cognito, create an Identity Pool for managing external identities. Fore more info, Azure AD workload identity federation with AWS | Identity in the cloud by uday

- Set up authentication providers in Cognito (e.g., OpenID Connect, Custom). Select Custom and provide a name of your choice in the Developer provider name. This custom provider option tells Cognito that authorized workloads using this developer provider name can get tokens for identities in this pool.

Step 2: Register the Federated Credential in Microsoft Entra ID
- Navigate to Microsoft Entra ID in the Azure portal.
- Create an Application Registration to represent the external workload.
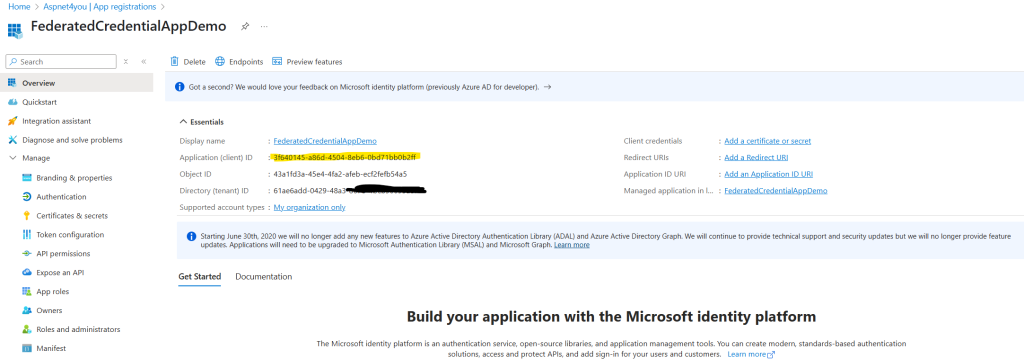
- Under the Federated Credentials section, register a new credential using AWS Cognito’s identity token issuer information.

- Use cognito-identity.amazonaws.com as issuer. When you got jwt token using get-open-id-token-for-developer-identity cli from AWS Cognito, it created an identity. Use this identity as Subject. Identity pool ID goes into audience field.

- Define permissions and roles for accessing Azure resources using Cognito-issued tokens.
Step 3: Implement Authentication in Workloads
- Configure your external workload (running in AWS) to retrieve Cognito-issued tokens. I am using aws cli from my laptop to get token from Cognito for this demo.

- Validate the received token with Entra ID to obtain necessary access permissions.

- Use the authenticated token to interact securely with Microsoft services like Azure Key Vault, Storage, or APIs.

Conclusion
Integrating Microsoft Entra ID Federated Credential with AWS Cognito unlocks a powerful federation model for cloud workloads, ensuring secure, scalable, and efficient authentication. Whether you’re managing multi-cloud environments or securing API-based applications, this approach provides a robust way to bridge identities across platforms without complex credential management.
Problem Solving
My initial attempt to use 2nd Azure Tenant as external identity provider did not work. It resulted in following error- AADSTS700226: Only MSI tokens may be used as Federated Identity Credentials for AAD issuer. I posted the question at stackoverflow to learn that you can’t use Azure as external tenant. You can but you have to use Managed Identity to get the initial token.
